CVE-2026-25137
NixOs Odoo database and filestore publicly accessible with default odoo configuration
Description
The NixOs Odoo package is an open source ERP and CRM system. From 21.11 to before 25.11 and 26.05, every NixOS based Odoo setup publicly exposes the database manager without any authentication. This allows unauthorized actors to delete and download the entire database, including Odoos file store. Unauthorized access is evident from http requests. If kept, searching access logs and/or Odoos log for requests to /web/database can give indicators, if this has been actively exploited. The database manager is a featured intended for development and not meant to be publicly reachable. On other setups, a master password acts as 2nd line of defence. However, due to the nature of NixOS, Odoo is not able to modify its own configuration file and thus unable to persist the auto-generated password. This also applies when manually setting a master password in the web-UI. This means, the password is lost when restarting Odoo. When no password is set, the user is prompted to set one directly via the database manager. This requires no authentication or action by any authorized user or the system administrator. Thus, the database is effectively world readable by anyone able to reach Odoo. This vulnerability is fixed in 25.11 and 26.05.
INFO
Published Date :
Feb. 2, 2026, 11:16 p.m.
Last Modified :
Feb. 3, 2026, 4:44 p.m.
Remotely Exploit :
Yes !
Source :
[email protected]
Affected Products
The following products are affected by CVE-2026-25137
vulnerability.
Even if cvefeed.io is aware of the exact versions of the
products
that
are
affected, the information is not represented in the table below.
No affected product recoded yet
CVSS Scores
| Score | Version | Severity | Vector | Exploitability Score | Impact Score | Source |
|---|---|---|---|---|---|---|
| CVSS 3.1 | CRITICAL | [email protected] |
Solution
- Update Odoo package to version 25.11 or later.
- Configure a master password for the database manager.
- Restrict access to the database manager interface.
- Review access logs for unauthorized database activity.
References to Advisories, Solutions, and Tools
Here, you will find a curated list of external links that provide in-depth
information, practical solutions, and valuable tools related to
CVE-2026-25137.
| URL | Resource |
|---|---|
| https://github.com/NixOS/nixpkgs/pull/485310 | |
| https://github.com/NixOS/nixpkgs/pull/485454 | |
| https://github.com/NixOS/nixpkgs/security/advisories/GHSA-cwmq-6wv5-f3px |
CWE - Common Weakness Enumeration
While CVE identifies
specific instances of vulnerabilities, CWE categorizes the common flaws or
weaknesses that can lead to vulnerabilities. CVE-2026-25137 is
associated with the following CWEs:
Common Attack Pattern Enumeration and Classification (CAPEC)
Common Attack Pattern Enumeration and Classification
(CAPEC)
stores attack patterns, which are descriptions of the common attributes and
approaches employed by adversaries to exploit the CVE-2026-25137
weaknesses.
We scan GitHub repositories to detect new proof-of-concept exploits. Following list is a collection of public exploits and proof-of-concepts, which have been published on GitHub (sorted by the most recently updated).
Results are limited to the first 15 repositories due to potential performance issues.
The following list is the news that have been mention
CVE-2026-25137 vulnerability anywhere in the article.

-
Daily CyberSecurity
AI Hub Hijacked: Polymorphic Android RAT Abuses Hugging Face to Steal Data
In a troubling convergence of trusted developer infrastructure and cybercrime, Bitdefender researchers have uncovered a sophisticated Android Remote Access Trojan (RAT) campaign that is turning the po ... Read more

-
Daily CyberSecurity
CVE-2026-25137: Critical Odoo on NixOS Flaw Exposes Databases
A critical vulnerability has been discovered in Odoo deployments running on NixOS. The vulnerability, tracked as CVE-2026-25137 (CVSS 9.1), leaves the database manager—and by extension, the entire org ... Read more
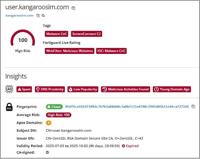
-
Daily CyberSecurity
Game Over: Interlock Ransomware Weaponizes Anti-Cheat Zero-Day to Kill EDR
FortiGuard Threat Intelligence details related to the ScreenConnect C2 domain associated with the intrusion | Image: FortiGuard Labs A sophisticated ransomware group known as Interlock is turning the ... Read more
The following table lists the changes that have been made to the
CVE-2026-25137 vulnerability over time.
Vulnerability history details can be useful for understanding the evolution of a vulnerability, and for identifying the most recent changes that may impact the vulnerability's severity, exploitability, or other characteristics.
-
New CVE Received by [email protected]
Feb. 02, 2026
Action Type Old Value New Value Added Description The NixOs Odoo package is an open source ERP and CRM system. From 21.11 to before 25.11 and 26.05, every NixOS based Odoo setup publicly exposes the database manager without any authentication. This allows unauthorized actors to delete and download the entire database, including Odoos file store. Unauthorized access is evident from http requests. If kept, searching access logs and/or Odoos log for requests to /web/database can give indicators, if this has been actively exploited. The database manager is a featured intended for development and not meant to be publicly reachable. On other setups, a master password acts as 2nd line of defence. However, due to the nature of NixOS, Odoo is not able to modify its own configuration file and thus unable to persist the auto-generated password. This also applies when manually setting a master password in the web-UI. This means, the password is lost when restarting Odoo. When no password is set, the user is prompted to set one directly via the database manager. This requires no authentication or action by any authorized user or the system administrator. Thus, the database is effectively world readable by anyone able to reach Odoo. This vulnerability is fixed in 25.11 and 26.05. Added CVSS V3.1 AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:H Added CWE CWE-306 Added CWE CWE-552 Added Reference https://github.com/NixOS/nixpkgs/pull/485310 Added Reference https://github.com/NixOS/nixpkgs/pull/485454 Added Reference https://github.com/NixOS/nixpkgs/security/advisories/GHSA-cwmq-6wv5-f3px


